objection
什么是Objection
Objection 是一种用于移动应用安全测试和逆向工程的开源工具,特别是针对 Android 应用程序。它提供了一套强大的功能和命令行工具,帮助安全研究人员、渗透测试人员和开发人员分析和评估移动应用的安全性。
一些 Objection 提供的功能包括:
Runtime Mobile Exploration(RME): 允许用户在设备上动态地探索和分析移动应用程序。可以在运行时修改应用程序的行为、检查内存中的变量等。
SSL Pinning Bypass: 可用于绕过应用程序中实现的 SSL Pinning 机制,从而更轻松地进行网络流量分析。
Frida Scripting: 集成了 Frida 功能,可以编写脚本来 Hook 和修改应用程序的行为。
API 集成: 可以通过 API 接口与 Objection 进行交互,使自动化测试和集成更容易。
数据解密和加密分析: 可以帮助用户解密应用程序中的数据,并分析加密算法和实现。
环境配置
1 | mkvirtualenv frida14 |
objection快速上手
注入命令
1 | objection -g 包名 explore |
启动前就hook
1 | objection -g 进程名 explore --startup-command "android hooking watch class 路径.类名" |
objection基础api
1 | memory list modules -查看内存中加载的库 |
1 | com.zj.wuaipojie on (OnePlus: 11) [usb] # memory list exports libandroidio.so |
1 | android hooking list activities -查看内存中加载的activity android hooking list services -查看内存中加载的services |
1 | android intent launch_activity 类名 -启动`activity`或`service`(可以用于一些没有验证的activity,在一些简单的ctf中有时候可以出奇效) |
1 | 关闭ssl校验 android sslpinning disable |
objection内存漫游
- 内存搜刮类实例
1 | com.zj.wuaipojie on (google: 13) [usb] # android heap search instances com.zj.wuaipojie.Demo |
- 调用实例的方法
无参数
1 | com.zj.wuaipojie on (google: 13) [usb] # android heap execute 127867717 getPublicInt |
有参数
1 | com.zj.wuaipojie on (google: 13) [usb] # android heap evaluate 127867717 |
- android hooking list classes -列出内存中所有的类(结果比静态分析的更准确)
这个列出的太多了,一般用不到 - android hooking search classes 关键类名 -在内存中所有已加载的类中搜索包含特定关键词的类
1 | com.zj.wuaipojie on (google: 13) [usb] # android hooking search classes wuaipojie |
- android hooking search methods 关键方法名 -在内存中所有已加载的类的方法中搜索包含特定关键词的方法(一般不建议使用,特别耗时,还可能崩溃)
- android hooking list class_methods 类名 -内存漫游类中的所有方法
1 | com.zj.wuaipojie on (google: 13) [usb] # android hooking list class_methods com.zj.wuaipojie.Demo |
objectionHook
hook类的所有方法
好像没什么效果
1 | com.zj.wuaipojie on (google: 13) [usb] # android hooking watch class com.zj.wuaipojie.Demo --dump-backtrace --dump-args |
- hook方法的参数、返回值和调用栈
1 | com.zj.wuaipojie on (google: 13) [usb] # android hooking watch class_method com.zj.wuaipojie.Demo.a --dump-args --dump- |
其他例子:
1 | android hooking watch class_method com.zj.wuaipojie.Demo.privateFunc --dump-args --dump-return --dump-backtrace |
- hook 类的构造方法
1 | android hooking watch class_method com.zj.wuaipojie.Demo.$init --dump-args --dump-backtrace |
- hook 方法的所有重载
1 | android hooking watch class_method com.zj.wuaipojie.Demo.repleaceFunc |
调用repleaceFunc的时候会显示
1 | (agent) [107162] Called com.zj.wuaipojie.Demo.repleaceFunc() |
trace实战java控制流混淆
项目地址:
BlackObfuscator
示例1: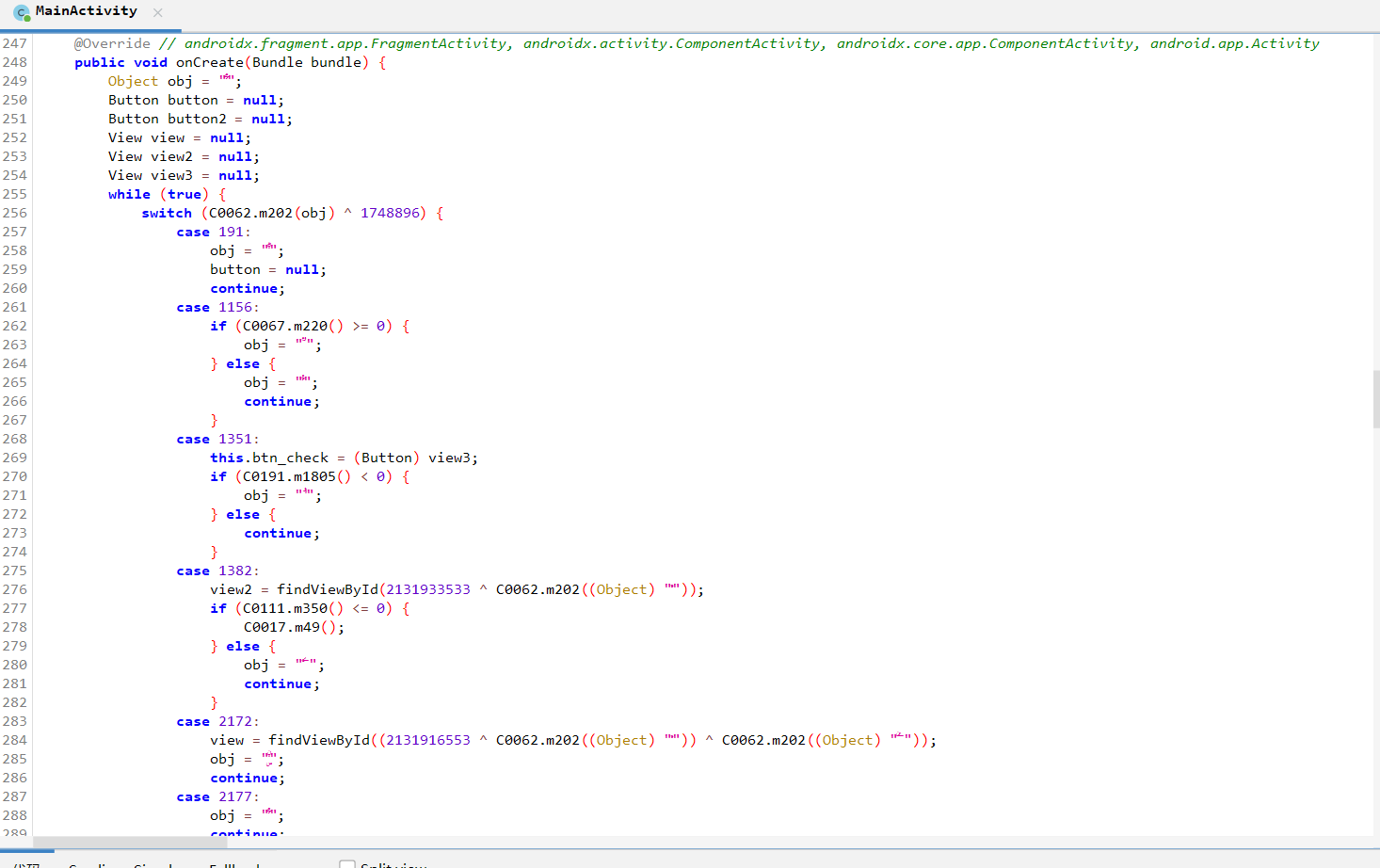
示例2:
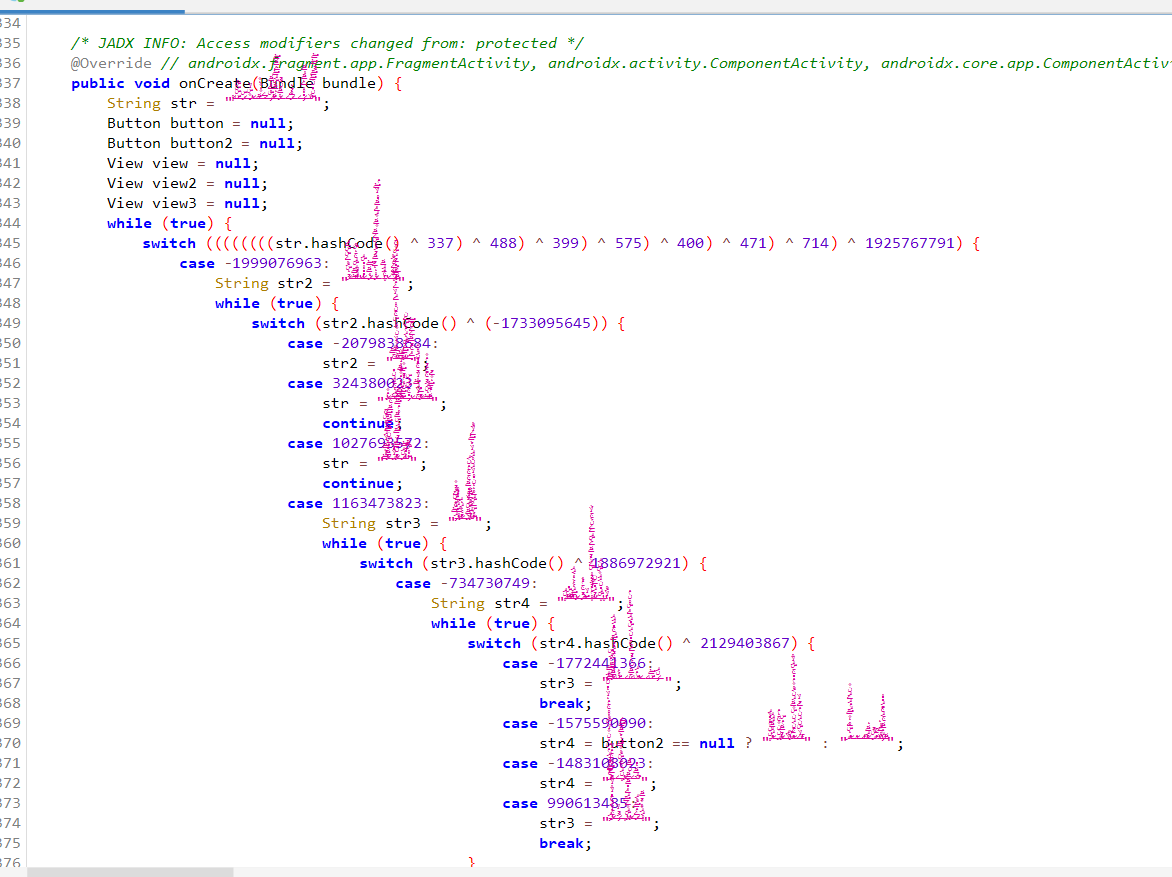
对抗方法
- ZenTracer
项目地址
缺点:无法打印调用栈,无法hook构造函数
支持frida的版本firda==14.2.18,可以通过frida-tools==9.2.4来安装
1 | pip install frida-tools==9.2.4 |
1 | //使用说明 |
具体使用实例
- 先启动frida-server
1 | OnePlus3:/data/local/tmp # ./frida-server-14.2.18-android-arm64 |
- 手机打开要分析的app
- 电脑端设置过滤
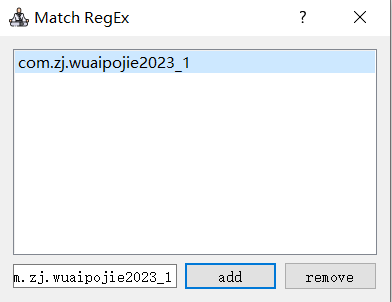
- 之后点击start,有下面的日志说明hook成功
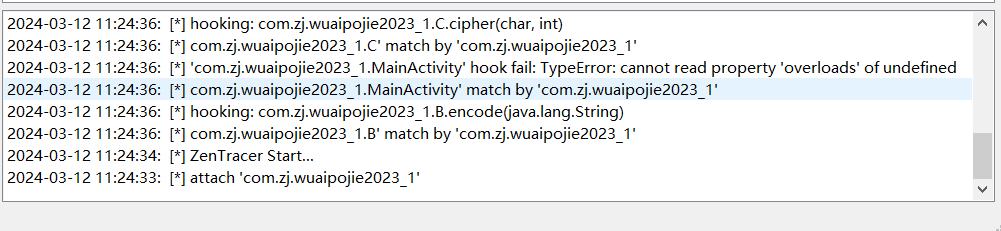
清空软件的log,点击app的功能(这里是flag验证)

就可以看到使用的加密算法,加密后的返回值,最终retval是
tips:可以导出json复制查看
- r0tracer
项目地址
- r0tracer
兼容最新版本frida,16.2.1
使用方法
- 修改r0tracer.js文件最底部处的代码,开启某一个Hook模式。
比如hook有wuaipojie2023_1关键字的所有类
1 | hook("wuaipojie2023_1"); |
- 推荐使用Frida14版本,并且将日志使用-o参数进行输出保存
1 | frida -U -f com.zj.wuaipojie2023_1 -l r0tracer.js --no-pause |
“-f”为Spawn模式,去掉”-f”为Attach模式
注意: hook不到类的话,还需要再app点击相应的功能,之后执行%reload一下,看看是否hook所有类
最开始也是只有4个类
1 | Search Class Completed! |
后面app点击相应的功能,之后执行%reload一下才hook7个
1 | Search Class Completed! |
- Frida版本=<12时,要加上–runtime=v8选项


